Hello everyone, we're back!
So in the past months things intensified at my job and one of the projects I have become project manager for is an attempt to hang up monitoring screens throughout the office. Have a small computer report on today's numbers. Think dashboards with revenue, new deals, security incidents (or lack thereof, proud moment!)
One of the candidates for a small computer to run these screens from is the Raspberry Pi. Some research went into setting it up and securing it, and I would like to share that with you all for this new security Saturday!
You should know that I tested several Linux flavors for the Pi. The two best, candidates were Raspberry Pi OS (the official OS) and Manjaro. Manjaro had a little less options for automating the setup and so my choice fell to be Raspberry Pi OS. Since Raspberry Pi OS starts you out with a passwordless administrator account, we better clean that up and set it up more securely, using a bash script.
First I was going to share a PDF (since that is possible now) with the Bash code in it, but setting that up looked to be way too much effort. Uploading the stuff and making a LaTeX implementation of the code is a pain as well, since it has a lot of same-line commentary. So instead, here is two images.
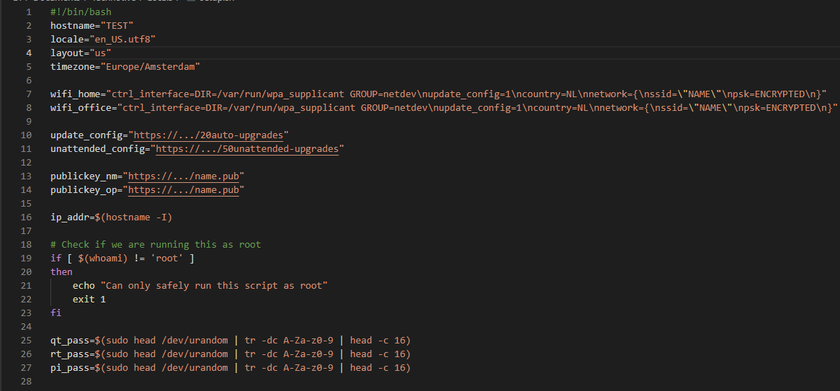
The first image is a layout of the variables the script will use, and the a pre-run check if the script is run as administrator (root is the Linux way of admin).
The first group of variables (hostname up to timezone) are to setup the Pi for use in our proper contacts (Dutch time, US keyboards, etc...) Then there is some (censored) wifi configuration one-liners to be written to configuration files. The third batch has censored web-addresses that pickup configuration files for the unattended-upgrades package that does the same-ish thing as windows auto-update. Then from the same source we pick up public keys to identify those people that are allowed to manage the Raspberry Pi. We will use these for identification, and not so much encryption (although to my understanding that implicitly also happens). Lastly we pick up the IP address of the Pi, before starting the script with the admin check.
After that (second image) you can pick up most of what is going on from the comment in the files. What I want you to notice is that many things are done by just adding to, or replacing text files. This is still one of the great strengths of Linux. Most config files are human-readable and adding or changing options is that simple.
In the process of the script, we generate new passwords, do some housekeeping on the device settings for quality-of-life improvements, and most notably, we obliterate the open-door setup with the Pi user having auto-login and no password requirement on "sudo" (Linux way of the "run as administrator" option on windows). Instead we create a new user called qt which can de passwordless sudo, but you can only login to the VV user using SSH, and only while having the right private key, belonging to the public key made known to the device in this script. The random password for this user is not at all remembered, and therefor one cannot use the password to login using mouse and keyboard.
This way we can give admin rights to all people managing these devices, without ever having to manage many passwords if the amount of screens increase. Which is pretty neat.
This script has some bugs still right now, but the prospects are amazing.
I know this is a very techie post, but hey, I am proud of the setup :)
There is so much more to this one chapter, but it is so good already!
I had to cut it short because guests arrived, but this should get you started on your own study :)
@calvinrempel Thank you once again for the Theology Tuesday you did, I refer back to it in this one :)
@JamesDerian Congratulations with your Marriage :)
Next time there might (almost certainly) not be a Theology Tuesday, so the official next one will be February 22nd! I have a marriage to attend. As the groom. Our home is still half a project.
Fun times!
This is the third corner to have persistent discussions and talks in. I love tech, but especially once it transcends hardware a little. I have two degrees; a bachelor's in Software Engineering and a master's in Information Security Technology. My graduation thesis focused on assembly-level optimizations (that is, one level above the hardware level) and my free subjects were in formal verification. This is why I love programming in the security corner, or maybe it is the other way around.
I started going down the Security path because I early on saw that the world around us would become a dangerous cesspool of badly-implemented and hostile tech. Now I am one of the people that understands the field around that mess :)
So in here you can discuss secure phones, weird programming languages, sad truths about internet-connected fridges. Also about malware, adblockers, and so on and so fort!
A lot of tech talk I do over at the @Lunduke community, where a lot of nerds hang out and it is ...
Much like the reading corner, let's have a music corner! A few rules for this one, since some music can be provocative. I don't mind much but let's keep youtube links with risque thumbnails out of here.
Other music I might also mind. "Do you find that offensive?" might someone ask. Yes, there is some music I choose not to listen on principle, and I walk a thin line there sometimes. But do not worry, I have a wide taste otherwise so feel free to share almost anything :)
Either way, here is the music corner!
Many times when we talk about security, we mean to say "Digital security". In essence we mean to say that our hardware and software that we use stays safe no matter what we do. And even though the ISO27001 standard (and by extension, for example, the NEN7510 standard) make it abundantly clear that security is a people-domain problem, we usually take that as a process-like truth. Meaning, we think that being secure is a matter of regulating people.
The truth is very different. For example, while writing this I am pretty shot. I slept five hours and I an under influence of a bunch of painkillers and some alcohol. Before you ask what I was thinking, let me mention that I have a genetic defect in my spine that I am dealing with right now by taking measured doses of all three (and yes, to get the Bible into this conversation, there is even a biblical ground for the inebriation with alcohol - see proverbs and the letters to Timothy - , although I did not use red wine. But hey, I am still on top of ...