Although I have been more quiet on this front (I think?) I do still tutor ~6 students in mathematics, and sometimes chemistry, physics and economics. For 3 of my students it is state exam time. Over the period mid-May 'till mid-June they will be taking several exams, among which is math, of course.
Now I recently got Aragorn, my new and fun iPad, which I use for teaching now. It is much fun to with with the Apple pen and draw some of the answers, and I am going to share a few and talk about them here. For those of you that are in a position to teach, maybe you will glean some ideas from here on how to morph explanations.
Exhibit one and two: Make your case explicit.
Theoretical mathematics is unnecessary in many cases. We live in a real world, and so to understand a case, we can use real numbers.
Example: Not everyone is fit to calculate percentages of percentages, because let's face it... Who in their right mind would take imaginary pieces of a number meant to take pieces from other numbers?
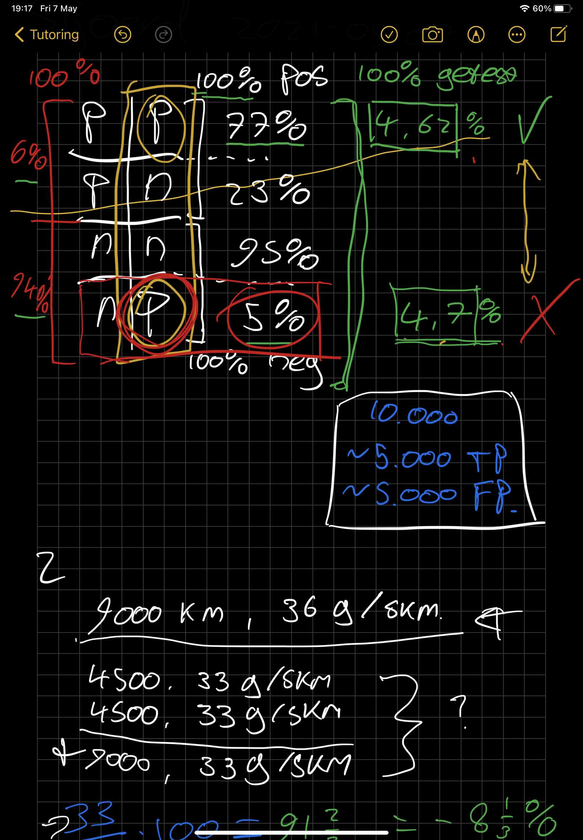
This exercise is about calculating false-positives and false-negatives in malaria tests (whoa, topical much? XD)
Exhibit 2: Use colors
You know, sometimes it is good to bring distinction and grouping, see the red dots? That is your square root disappearing due to the red operation (square on both sides). See the blue dots? That is your constant factor getting eliminated by your blue operation (divide by 9.8)
This exercise asks the student to calculate the input to the function, given some outcome. Not that solving for [been] is only one option, the other is squeezing the function by (essentially) doing a binary search with potential answers. The latter is possible because you know you have to round to centimeters, which makes your decimal steps finite.
Again, point and case that theoretical math (there is no limit to division, real numbers are infinitely infinite) rarely has a place in teaching.
Exhibit three: Divide and conquer
In this case the student is asked to see if two separate formulas that try to describe the same phenomenon can have diametrically opposed answers in some cases.
Instead of trying to pit them against eachother directly, ask instead: In which domain is function "Ia" true? In which domain is function "Ic" false? Do these have overlap?
Now I did a poor job of explaining that last situation, but (I hope) I learned from it.
Now, for me it is two more weeks of tutoring before I can say goodbye to half of my students.
I might miss them, I don't know yet :P
There is so much more to this one chapter, but it is so good already!
I had to cut it short because guests arrived, but this should get you started on your own study :)
@calvinrempel Thank you once again for the Theology Tuesday you did, I refer back to it in this one :)
@JamesDerian Congratulations with your Marriage :)
Next time there might (almost certainly) not be a Theology Tuesday, so the official next one will be February 22nd! I have a marriage to attend. As the groom. Our home is still half a project.
Fun times!
This is the third corner to have persistent discussions and talks in. I love tech, but especially once it transcends hardware a little. I have two degrees; a bachelor's in Software Engineering and a master's in Information Security Technology. My graduation thesis focused on assembly-level optimizations (that is, one level above the hardware level) and my free subjects were in formal verification. This is why I love programming in the security corner, or maybe it is the other way around.
I started going down the Security path because I early on saw that the world around us would become a dangerous cesspool of badly-implemented and hostile tech. Now I am one of the people that understands the field around that mess :)
So in here you can discuss secure phones, weird programming languages, sad truths about internet-connected fridges. Also about malware, adblockers, and so on and so fort!
A lot of tech talk I do over at the @Lunduke community, where a lot of nerds hang out and it is ...
Much like the reading corner, let's have a music corner! A few rules for this one, since some music can be provocative. I don't mind much but let's keep youtube links with risque thumbnails out of here.
Other music I might also mind. "Do you find that offensive?" might someone ask. Yes, there is some music I choose not to listen on principle, and I walk a thin line there sometimes. But do not worry, I have a wide taste otherwise so feel free to share almost anything :)
Either way, here is the music corner!
Many times when we talk about security, we mean to say "Digital security". In essence we mean to say that our hardware and software that we use stays safe no matter what we do. And even though the ISO27001 standard (and by extension, for example, the NEN7510 standard) make it abundantly clear that security is a people-domain problem, we usually take that as a process-like truth. Meaning, we think that being secure is a matter of regulating people.
The truth is very different. For example, while writing this I am pretty shot. I slept five hours and I an under influence of a bunch of painkillers and some alcohol. Before you ask what I was thinking, let me mention that I have a genetic defect in my spine that I am dealing with right now by taking measured doses of all three (and yes, to get the Bible into this conversation, there is even a biblical ground for the inebriation with alcohol - see proverbs and the letters to Timothy - , although I did not use red wine. But hey, I am still on top of ...